Enterprise Web & Infrastructure Protection
Enterprise Web & Infrastructure Protection
Incapsula vs F5
The Enterprise Web & Infrastructure Protection’ is for an enterprise that needs to protect both the website and network assets (VPNs, Class C networks, etc). Enterprises that look for an end-to-end DDoS solution will require web protection (DNS-based), infrastructure protection (BGP-based), and possibly even an on-premises appliance. The annual budget for a DDoS solution would start at a range of $50-100K.
In this report, two vendors provide a ‘full-scale enterprise’ solution: F5 Silverline and Incapsula. CloudFlare was not included because we did not have sufficient data to warrant if its infrastructure protection is good enough to enter the category.

Deployment & Service Options
Diversion Method: DNSNo posts could be found that matched the specified criteria. |
||||
Always-onNo posts could be found that matched the specified criteria. |
||||
On-demandNo posts could be found that matched the specified criteria. |
||||
Non-web protocolsNo posts could be found that matched the specified criteria. |
(IP Protection) | Both vendors support non- web protocols. | ||
Diversion Method: BGPNo posts could be found that matched the specified criteria. |
||||
Always-onNo posts could be found that matched the specified criteria. |
||||
On-demandNo posts could be found that matched the specified criteria. |
||||
|
Service Features |
||||
SSL support – HSMNo posts could be found that matched the specified criteria. |
||||
Emergency responseNo posts could be found that matched the specified criteria. |
||||
Fully managed serviceNo posts could be found that matched the specified criteria. |
F5 offers fully managed service. | |||
Number of Data CentersNo posts could be found that matched the specified criteria. |
30 see locations | 4
see locationsNo posts could be found that matched the specified criteria. |
Incapsula has 30 data centers, F5 has only 4. |
Diversion Method: DNSNo posts could be found that matched the specified criteria. |
||||
Always-onNo posts could be found that matched the specified criteria. |
||||
On-demandNo posts could be found that matched the specified criteria. |
||||
Non-web protocolsNo posts could be found that matched the specified criteria. |
(IP Protection) | Both vendors support non- web protocols. | ||
Diversion Method: BGPNo posts could be found that matched the specified criteria. |
||||
Always-onNo posts could be found that matched the specified criteria. |
||||
On-demandNo posts could be found that matched the specified criteria. |
||||
|
Service Features |
||||
SSL support – HSMNo posts could be found that matched the specified criteria. |
||||
Emergency responseNo posts could be found that matched the specified criteria. |
||||
Fully managed serviceNo posts could be found that matched the specified criteria. |
F5 offers fully managed service. | |||
Number of Data CentersNo posts could be found that matched the specified criteria. |
30 see locations | 4
see locationsNo posts could be found that matched the specified criteria. |
Incapsula has 30 data centers, F5 has only 4. |
Incapsula vs. F5 – Deployment
Incapsula Enterprise and F5 Silverline deployment options are very similar. Both offer DNS and BGP-based diversion, a solution for non-web protocols, and On-Demand and Always-On. F5 offers fully managed service, whereas Incapsula is only partially managed. Although not directly effecting DDoS, Incapsula offers web acceleration and has 30 POPs vs. F5 which only has 4 POPs. This can also effect organizations that do not wish to accelerate but only maintain their existing latency.
Mitigation
The Web Protection of both vendors is extremely good. They are both fully or almost fully loaded with all the required protection.
The Infrastructure Protection of both F5 and Incapsula is based on a black-box approach, which is less than perfect. Realistically, though, this is the common practice in cloud services.
Proxy / CachingNo posts could be found that matched the specified criteria. |
||||
Reverse ProxyNo posts could be found that matched the specified criteria. |
||||
CachingIn DDoS mitigation, web caching is done by reverse-proxies which act in tandem as prominent line of defense by blocking attacks from reaching the web server. (read more) |
||||
Web ChallengesNo posts could be found that matched the specified criteria. |
F5 is the only one offering the entire web challenge spectrum. | |||
Cookie ValidationNo posts could be found that matched the specified criteria. |
||||
JavaScript ChallengeNo posts could be found that matched the specified criteria. |
||||
Silent Bot DetectionNo posts could be found that matched the specified criteria. |
||||
Modern CAPTCHANo posts could be found that matched the specified criteria. |
||||
CAPTCHANo posts could be found that matched the specified criteria. |
||||
SignaturesNo posts could be found that matched the specified criteria. |
||||
VendorNo posts could be found that matched the specified criteria. |
||||
CustomerNo posts could be found that matched the specified criteria. |
||||
Blacklist (BL) / WhitelistNo posts could be found that matched the specified criteria. |
||||
|
BL IP |
||||
|
BL URL |
||||
|
BL Geo-protection |
||||
|
Whitelist |
||||
Rate LimitNo posts could be found that matched the specified criteria. |
||||
|
IP |
||||
|
URL |
||||
|
Geo-protection |
||||
|
DNS |
||||
DNS protectionNo posts could be found that matched the specified criteria. |
||||
|
SCORE |
96% | 100% | Both vendors have excellent mitigation technology coverage. |
Proxy / CachingNo posts could be found that matched the specified criteria. |
||||
Reverse ProxyNo posts could be found that matched the specified criteria. |
||||
CachingIn DDoS mitigation, web caching is done by reverse-proxies which act in tandem as prominent line of defense by blocking attacks from reaching the web server. (read more) |
||||
Web ChallengesNo posts could be found that matched the specified criteria. |
F5 is the only one offering the entire web challenge spectrum. | |||
Cookie ValidationNo posts could be found that matched the specified criteria. |
||||
JavaScript ChallengeNo posts could be found that matched the specified criteria. |
||||
Silent Bot DetectionNo posts could be found that matched the specified criteria. |
||||
Modern CAPTCHANo posts could be found that matched the specified criteria. |
||||
CAPTCHANo posts could be found that matched the specified criteria. |
||||
SignaturesNo posts could be found that matched the specified criteria. |
||||
VendorNo posts could be found that matched the specified criteria. |
||||
CustomerNo posts could be found that matched the specified criteria. |
||||
Blacklist (BL) / WhitelistNo posts could be found that matched the specified criteria. |
||||
|
BL IP |
||||
|
BL URL |
||||
|
BL Geo-protection |
||||
|
Whitelist |
||||
Rate LimitNo posts could be found that matched the specified criteria. |
||||
|
IP |
||||
|
URL |
||||
|
Geo-protection |
||||
|
DNS |
||||
DNS protectionNo posts could be found that matched the specified criteria. |
||||
|
SCORE |
96% | 100% | Both vendors have excellent mitigation technology coverage. |
Incapsula vs. F5 – Mitigation
UX and Reporting
Incapsula has a clear advantage with user experience (UX). F5 Silverline configuration screens seem to have paused in the “network appliance age”, with certain screens of the Cloud WAF service resembling the F5 ASM product.
To balance this picture slightly, F5 Silverline real-time traffic monitoring screens are much better.
When you deploy a new web asset to protect the UX will be better with Incapsula. However, if you want to protect a new network, with F5 it is a self-service and with Incapsula you need full-service.
In forensics, F5 has an advantage, while Incapsula will provide you the basic alert details, with F5 you can get the event capture file, you can also record the traffic in real time and even instantly open a request to investigate by their SOC.
Look and FeelNo posts could be found that matched the specified criteria. |
Excellent | Basic | Incapsula’s look and feel and ease of navigation is much better than F5’s. | |
|
Ease-of-Navigation |
Excellent | Basic | ||
|
Deployment |
||||
|
New website (DNS) |
Excellent | Basic | ||
|
New network (BGP) |
Full Service |
Excellent | ||
|
Security |
||||
|
Block IP (BGP) |
Excellent | Excellent | ||
|
Block URL |
Excellent | Good | ||
Web ChallengeNo posts could be found that matched the specified criteria. |
Excellent | Basic | ||
Signatures (vendor)No posts could be found that matched the specified criteria. |
Signatures (vendor) | Basic | Incapsula’s user signatures ‘IncapRules’ is both powerful and intuitive. F5’s ‘iRules’ is powerful but less intuitive. | |
Signatures (customer)No posts could be found that matched the specified criteria. |
Excellent | Good | ||
|
Security |
||||
|
Real Traffic |
Excellent | Excellent | ||
|
Blocked Traffic |
Excellent | Excellent | ||
|
Response Time |
Excellent | Unknown | ||
|
Events |
||||
|
Web logs |
Excellent | Excellent | ||
|
|
||||
|
Call |
||||
|
Syslog |
||||
|
REST |
||||
ForensicsDDoS Forensics is the digital forensic process to better understand a DDoS attack, past or-going. The output of forensics can shed light on the attack vectors, attack tools and the attacker characteristics or identity. ARE YOU READY?Answer seven online questions and get a free report assessing your protection status with recommendations for improvement |
F5 provides decent forensics with capture files (real-time and per-event). | |||
|
Detailed alertn |
Excellent | Excellent | ||
|
Event capture file |
Good | |||
|
RT capture file |
Full | |||
|
SCORE |
77% | 65% |
Look and FeelNo posts could be found that matched the specified criteria. |
Excellent | Basic | Incapsula’s look and feel and ease of navigation is much better than F5’s. | |
|
Ease-of-Navigation |
Excellent | Basic | ||
|
Deployment |
||||
|
New website (DNS) |
Excellent | Basic | ||
|
New network (BGP) |
Full Service |
Excellent | ||
|
Security |
||||
|
Block IP (BGP) |
Excellent | Excellent | ||
|
Block URL |
Excellent | Good | ||
Web ChallengeNo posts could be found that matched the specified criteria. |
Excellent | Basic | ||
Signatures (vendor)No posts could be found that matched the specified criteria. |
Signatures (vendor) | Basic | Incapsula’s user signatures ‘IncapRules’ is both powerful and intuitive. F5’s ‘iRules’ is powerful but less intuitive. | |
Signatures (customer)No posts could be found that matched the specified criteria. |
Excellent | Good | ||
|
Security |
||||
|
Real Traffic |
Excellent | Excellent | ||
|
Blocked Traffic |
Excellent | Excellent | ||
|
Response Time |
Excellent | Unknown | ||
|
Events |
||||
|
Web logs |
Excellent | Excellent | ||
|
|
||||
|
Call |
||||
|
Syslog |
||||
|
REST |
||||
ForensicsDDoS Forensics is the digital forensic process to better understand a DDoS attack, past or-going. The output of forensics can shed light on the attack vectors, attack tools and the attacker characteristics or identity. ARE YOU READY?Answer seven online questions and get a free report assessing your protection status with recommendations for improvement |
F5 provides decent forensics with capture files (real-time and per-event). | |||
|
Detailed alertn |
Excellent | Excellent | ||
|
Event capture file |
Good | |||
|
RT capture file |
Full | |||
|
SCORE |
77% | 65% |
Incapsula vs. F5 – UX & Reporting
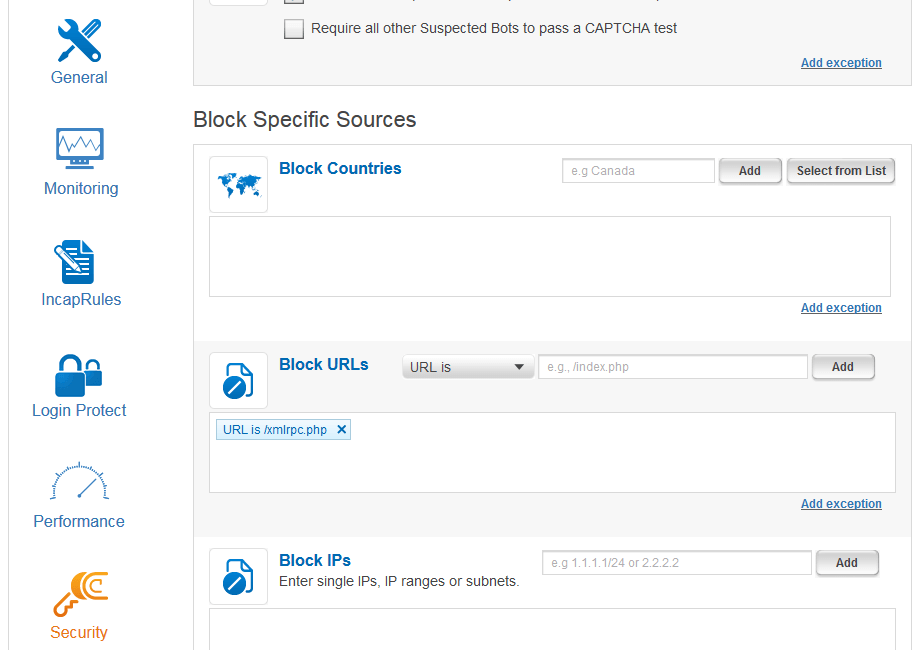
Incapsula vs. F5 – An Incapsula security
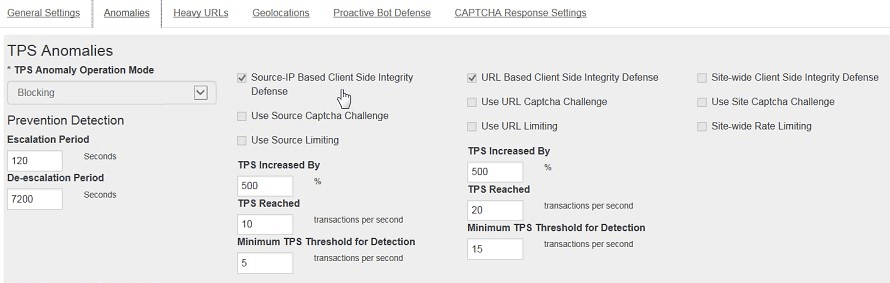
An F5 security configuration screen.
Pricing
Both vendors do not publicly provide their enterprise plans. Their pricing factors are relatively similar. The only difference is that Incapsula also adds attack traffic as a pricing factor, which we consider a disadvantage (see Customer Oriented Pricing Model).
Bottom line
The technical comparison of the two vendors shows that there is no clear-cut conclusion. Both vendors offer rich deployment and mitigation options.
Enterprises looking for a fully-managed service will find a better home with F5. The user-interface of Incapsula is clearly better and today this is not a luxury item anymore.
Another factor that may be relevant in the decision is that Incapsula offers a CDN while F5 Silverline does not. This can also be a critical advantage if you need the data center to be in specific geographical areas either due to regulation or to reduce latency.
| How to make a decision? | • Receive quote. • Investigate the stability and support of reach vendor. • Read the How to Complete the Vendor Selection Section |
Addional Relevant Chapters:
- Individual vendor reviews: Incapsula, F5
- Next steps – completing your evaluation
Addional Relevant Chapters:
- Individual vendor reviews: Incapsula, F5
- Next steps – completing your evaluation
Newsletter
Stay up to day with the latest DDoS news
Error: Contact form not found.