We begin with an exploration call to learn about your architecture, DDoS protection measures and goals. We then plan simulations that best suit the situation, with controlled attacks and coordination with your team. After the tests have been executed, we provide a detailed report of the results, including which attacks were not mitigated, their severity, and recommendations on how to improve your defenses. We review these results in a conference call and answer any questions you may have.
The Most Realistic
DDoS Simulation Testing
Harden your DDoS defenses against the tactics
and strategies of top hackers.


What Our Customers Say:
Find Out What Your DDoS Protection Is Really Worth
Challenge your system with hacker-like DDoS simulations:
- Large multi-gigabit traffic volume from multiple global sources.
- The latest, most sophisticated attacks, leveraging our incident response expertise.
- Customized tests that stress your system architecture at its
weakest points.
Harden Your Defenses
Fix all faults detected during the DDoS simulations:
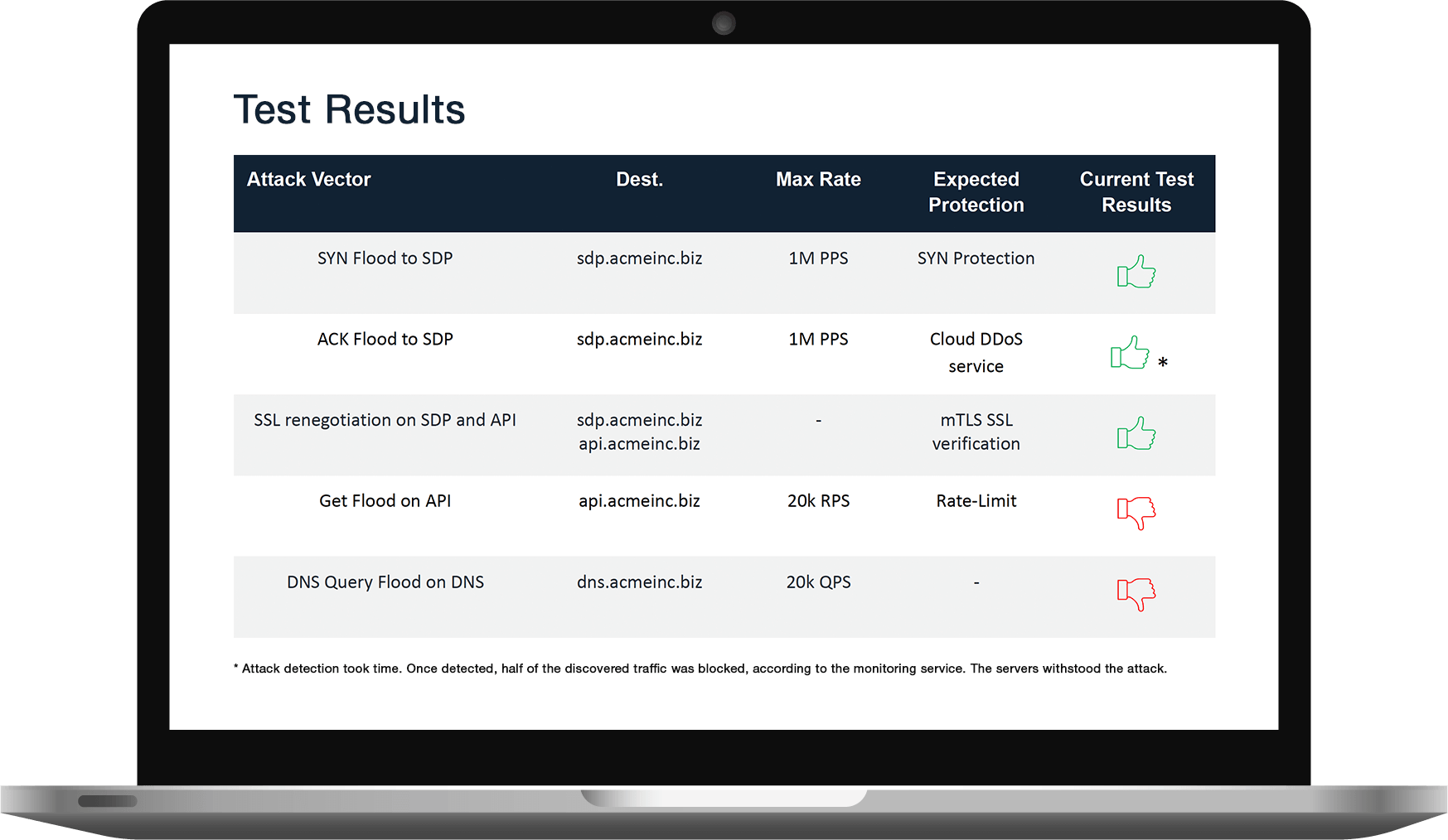
- Test reports list all defense vulnerabilities, prioritized by severity. See a test report example.
- Actionable recommendations and retests help you close the identified gaps.
- Our expert team helps you fix configuration and architecture changes.
Get Results with
Near-Zero Effort
Our fully managed DDoS testing service saves you
time and resources:
- Test planning, execution and analysis performed by our highly experienced DDoS experts.
- A total of five hours of your time: One hour for pre-test interview, three hours for test session, and one hour for reporting the results and our recommendations.

FAQ
We will confirm that your ISP, cloud providers, mitigators and data center have agreed to the DDoS testing details. Because we are an authorized DDoS Test Partner of both AWS and Azure, we have standing approval from them to carry out DDoS tests (up to a certain volume of traffic) at any time, without the need for further notifications or permissions.
Because we use a white box testing approach to design DDoS attacks that stress your specific architecture, we first learn about your services, network, and mitigation technologies. This helps us plan effective tests, as well as provide actionable recommendations for your environment.
Our tests are designed to simulate real-life attacks, based on the latest tactics and strategies of global hackers. They combine multiple attack vectors:
- Volumetric attacks from multiple global locations to test your ability to withstand extreme and sustained campaigns with massive traffic.
- Protocol (network-layer) attacks such as SYN floods, UDP floods, and others.
- Application-layer attacks that test your resistance to the more difficult-to-detect, layer 7 attacks.
The risks are minimal. We employ multiple methods and procedures to minimize disruption and keep you in full control during test simulations. For example, testing can be limited to your pre-production system and carried out during maintenance windows. During a DDoS test, we increase attack rates gradually while monitoring your system’s response, and we can stop the attack immediately in case of any undesired impact.
No. Our DDoS attack simulation is a fully managed service. There is no need to install any software.
Yes. Since DDoS simulation tests are carried out with the knowledge and approval of the targeted organization, they are considered a legal activity. Read more about this here.
