Technology Hardening
Improve your network architecture against attacks and optimize
your DDoS appliance configuration.
Network Architecture
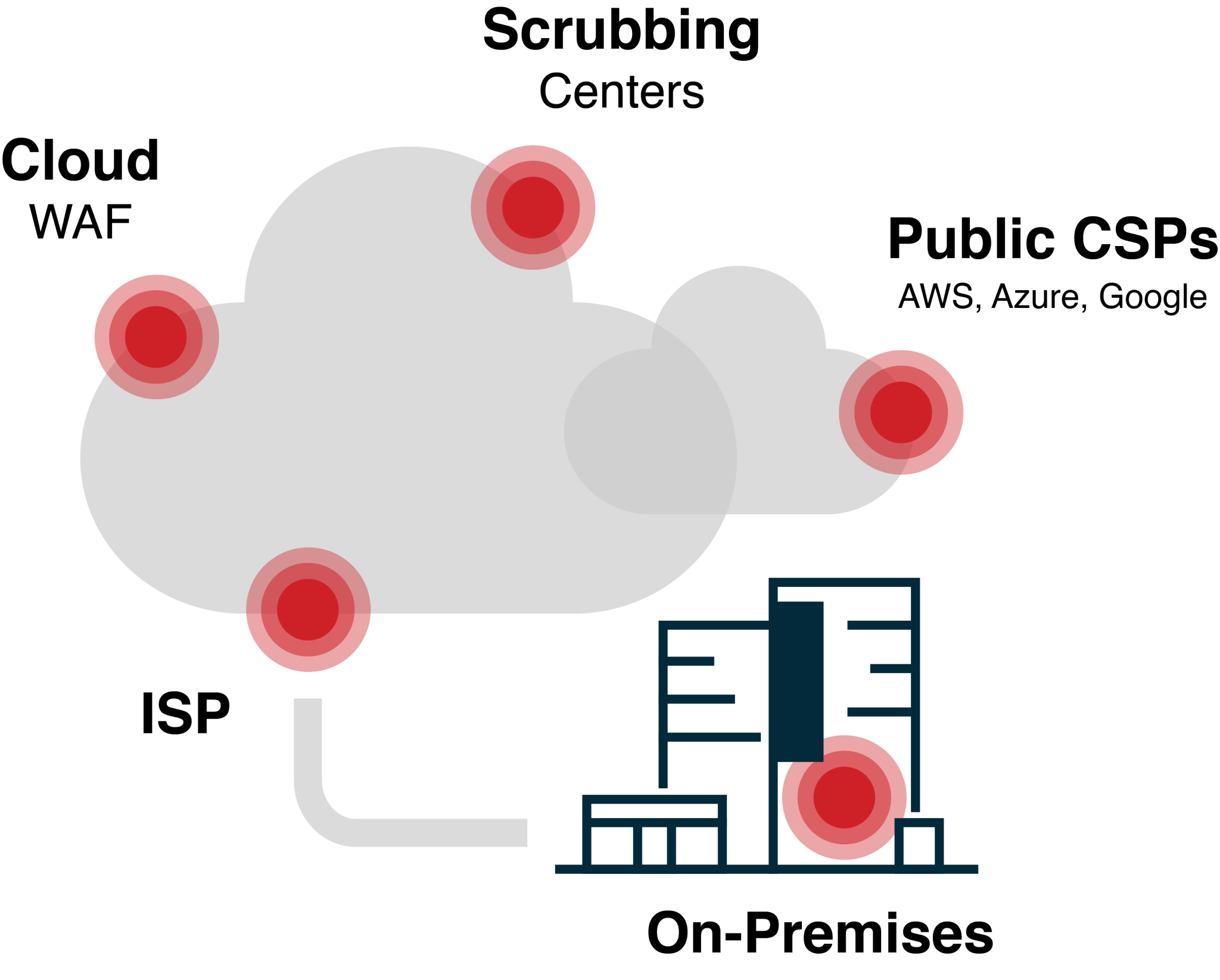
Our experts audit your DDoS network architecture infrastructure to identify weaknesses and provide recommendations for maximizing DDoS protection. This step, taken regardless of which vendor you use, ensures a solid foundation for DDoS protection, with the right components in the right locations.
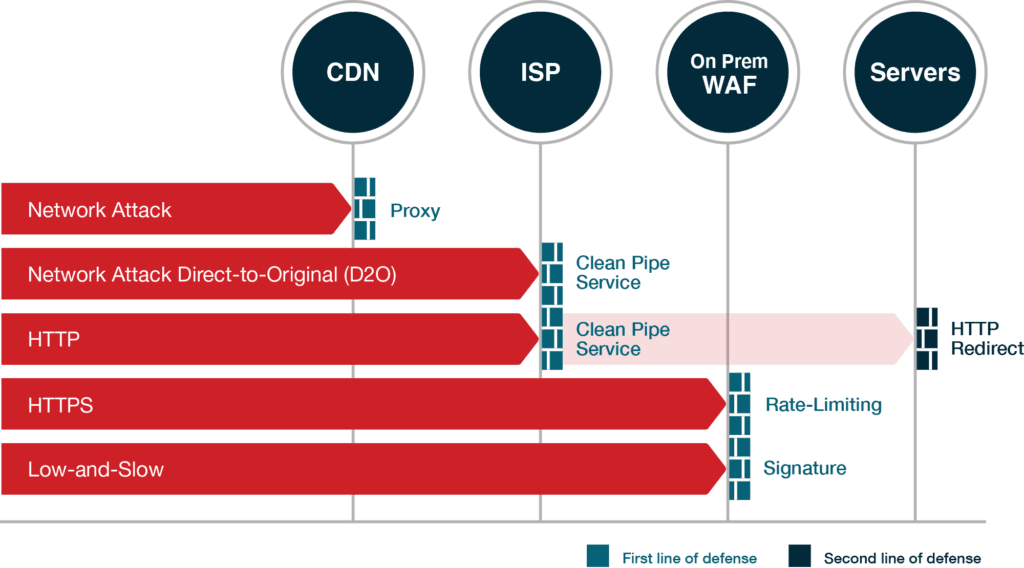
Attack Vector Analysis
We identify which protection component will prevent each DDoS attack vector.
Configuration Optimization
Installed DDoS protection solutions are often underutilized. Our team dives into your protection setup and provides detailed instructions on how to improve appliance configuration.
For example, we ensure that rate limit thresholds are well-calibrated, that you have chosen the most appropriate web challenge, and that you fully utilize bot and geo-protection.